Sherlock
- Thiru T
- Nov 8, 2024
- 1 min read
PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities.
Supports:
MS10-015 : User Mode to Ring (KiTrap0D)
MS10-092 : Task Scheduler
MS13-053 : NTUserMessageCall Win32k Kernel Pool Overflow
MS13-081 : TrackPopupMenuEx Win32k NULL Page
MS14-058 : TrackPopupMenu Win32k Null Pointer Dereference
MS15-051 : ClientCopyImage Win32k
MS15-078 : Font Driver Buffer Overflow
MS16-016 : 'mrxdav.sys' WebDAV
MS16-032 : Secondary Logon Handle
MS16-034 : Windows Kernel-Mode Drivers EoP
MS16-135 : Win32k Elevation of Privilege
CVE-2017-7199 : Nessus Agent 6.6.2 - 6.10.3 Priv Esc
Install: (PowerShell)
# Git install
git clone https://github.com/rasta-mouse/Sherlock
# Load powershell module
Import-Module -Name C:\INSTALL_LOCATION\Sherlock\Sherlock.ps1Usage: (PowerShell)
# Run all functions
Find-AllVulns
# Run specific function (MS14-058 : TrackPopupMenu Win32k Null Pointer Dereference)
Find-MS14058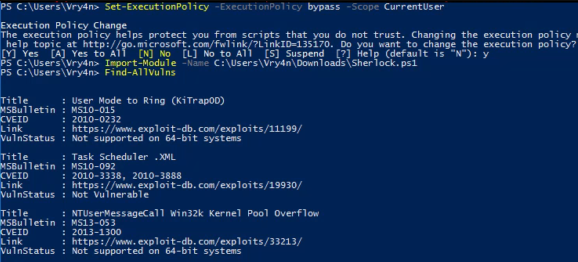



Comments